Introduction and Background
This article is a companion to the “HowTo: Check Citrix Workspace App for Win Version with EPA Scan on Citrix ADC” article written previously. It expands upon the logic to include checking for CWA versions on different OSs such as Windows, Mac, and Linux. The means for identifying the CWA version will differ between OSs.
The setup of this article is presented as follows. For additional context please visit the original article.
- EPA check action for Windows
- EPA check action for MacOS
- EPA check action for Linux
- Policy Label and policies for selecting the right EPA check based on OS user agent (which will be derived from the EPA client)
A note on Linux: The client must be installed in the default location per the installer to work. It should also be noted clearly dear reader, that the Linux check will not work consistently on all Linux distributions. We tested successfully the file date check on Ubuntu and CentOS, however, distributions such as Arch set the file dates to the date of installation, which will lead to false positives. Until a better method is identified please bear in mind that on some distributions of Linux, the compliance check may be of limited use and may indicate clients are compliant even if they installed a non-compliant version of CWA recently (whose install date was at or later than the minimum file data your EPA scan is checking for).
EPA Check Action for Windows
This is a re-use from the original article, included for completeness. This action will check for 2203 LTSR or higher. Add / modify to match your supported version(s). Check the original article for caveats on how the version check is used.
add authentication epaAction epa_cwa-ver-chk-win_act -csecexpr q/(sys.client_expr("sys_0_REG_PATH_==_HKEY\\\\_LOCAL\\\\_MACHINE\\\\\\\\SOFTWARE\\\\\\\\WOW6432Node\\\\\\\\Microsoft\\\\\\\\Windows\\\\\\\\CurrentVersion\\\\\\\\Uninstall\\\\\\\\CitrixOnlinePluginPackWeb\\\\\\\\VersionMajor_VALUE_==_22[COMMENT: Registry]")) && (sys.client_expr("sys_0_REG_PATH_==_HKEY\\\\_LOCAL\\\\_MACHINE\\\\\\\\SOFTWARE\\\\\\\\WOW6432Node\\\\\\\\Microsoft\\\\\\\\Windows\\\\\\\\CurrentVersion\\\\\\\\Uninstall\\\\\\\\CitrixOnlinePluginPackWeb\\\\\\\\VersionMinor_VALUE_>=_3[COMMENT: CWA 2203 or higher]"))/
EPA Check for MacOS
This action will check for a file version of the CWA client installed in MacOS. This method appears to be reliable based on various CWA for Mac client version installs conducted during development. In this example we are looking for CWA for Mac 2211 or higher. As new versions arise, install CWA on a Mac endpoint and examine the new file time on the subject file “Citrix Workspace” located at “/Applications/Citrix Workspace.app/Contents/MacOS/” within the file system.
add authentication epaAction epa_cwa-ver-chk-mac_act -csecexpr "sys.client_expr(\"filetime_0_/Applications/Citrix Workspace.app/Contents/MacOS/Citrix Workspace_20221103dt[COMMENT: CWA ver. 2211 or higher]\")"
EPA Check for Linux
This action is similar in logic to the MacOS scan but is checking the file date of the SelfService file located at /opt/Citrix/ICAClient/. In this case we are checking for CWA for Linux 2211 or higher. Note the caveats mentioned above pertaining to a reliance on the default client install location, and that not all Linux distributions honour the timestamp of the original installation binaries.
add authentication epaAction epa_cwa-ver-chk-linux_act -csecexpr "sys.client_expr(\"filetime_0_/opt/Citrix/ICAClient/selfservice_20221107dt[COMMENT: CWA ver. 2211 or higher]\")"
EPA Check Selector
This ties everything together and can be lined to the AAA-TM vServer after a previous policy binding. Otherwise, if the EPA scan happens first, can do without this PL and bind all the policies below directly to the AAA-TM vServer. I would suggest considering the initial factor to be a NOAUTHN policy and linking this policy label however, due to historical experience with preauth EPA scans causing sporadic failures if authentication with Workspace App vs. browser. This Policy Label will select the appropriate EPA check policy based on User Agent of the EPA client on the endpoint. If all fail, the user will match with the “failed” policy which will send them to an “access denied” page with a Login Schema configured to block the user from logging in and terminate the authentication flow. For the details of that policy, theme customization (for the custom label) to make it happen, and login schema, please visit the original article.
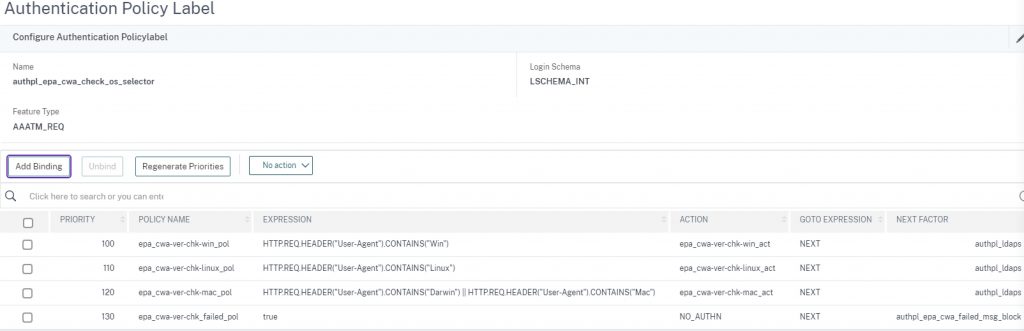
Note that before creating the configurations below, you’ll want to ensure you have a “next factor” reference to send successful scans down the authentication flow. This example uses an LDAPS factor. Similarly, for the failure policy, you’ll want to ensure you’ve created the EPA scan failure policy label, login schema, and custom label in advance. Consider the next factor for that one a placeholder in this config.
add authentication policylabel authpl_epa_cwa_failed_msg_block -loginSchema lschema_epa_cwa_block add authentication policylabel authpl_epa_cwa_check_os_selector -loginSchema LSCHEMA_INT add authentication Policy epa_cwa-ver-chk-win_pol -rule "HTTP.REQ.HEADER(\"User-Agent\").CONTAINS(\"Win\")" -action epa_cwa-ver-chk-win_act add authentication Policy epa_cwa-ver-chk-linux_pol -rule "HTTP.REQ.HEADER(\"User-Agent\").CONTAINS(\"Linux\")" -action epa_cwa-ver-chk-linux_act -comment "Linux CWA must be installed within default path. Path is default on all distros." add authentication Policy epa_cwa-ver-chk-mac_pol -rule "HTTP.REQ.HEADER(\"User-Agent\").CONTAINS(\"Darwin\") || HTTP.REQ.HEADER(\"User-Agent\").CONTAINS(\"Mac\")" -action epa_cwa-ver-chk-mac_act bind authentication policylabel authpl_epa_cwa_check_os_selector -policyName epa_cwa-ver-chk-win_pol -priority 100 -gotoPriorityExpression NEXT -nextFactor authpl_ldaps bind authentication policylabel authpl_epa_cwa_check_os_selector -policyName epa_cwa-ver-chk-linux_pol -priority 110 -gotoPriorityExpression NEXT -nextFactor authpl_ldaps bind authentication policylabel authpl_epa_cwa_check_os_selector -policyName epa_cwa-ver-chk-mac_pol -priority 120 -gotoPriorityExpression NEXT -nextFactor authpl_ldaps bind authentication policylabel authpl_epa_cwa_check_os_selector -policyName epa_cwa-ver-chk_failed_pol -priority 130 -gotoPriorityExpression NEXT -nextFactor authpl_epa_cwa_failed_msg_block
Conclusion
The configuration should now be ready for testing using different OS endpoints. The actions should be maintained periodically to accommodate for changes in the organization’s accepted compliance standards for the Citrix Workspace app.
Big thanks to our talented team members Stan Demburg and Michael Wieloch for the development and testing of this solution.
Bonus – Revised Login Schema
For those interested in the associated lschema to display a message reflecting the minimum CWA versions being checked for, you may find it below. Remember, the custom label configuration is still required in order to properly terminate the authentication flow and flip the user back to the login page via the “Cancel” button.
<?xml version="1.0" encoding="UTF-8"?> <AuthenticateResponse xmlns="http://citrix.com/authentication/response/1"> <Status>success </Status> <Result>more-info</Result> <StateContext/> <AuthenticationRequirements> <CancelPostBack>/nf/auth/doLogoff.do</CancelPostBack> <CancelButtonText>Cancel</CancelButtonText> <Requirements> <Requirement><Credential><Type>none</Type></Credential><Label><Text>ACCESS DENIED - NON-COMPLIANT CITRIX CLIENT</Text><Type>heading</Type></Label><Input /></Requirement> <Requirement><Credential><Type>none</Type></Credential><Label><Text>Your Citrix Workspace App is not at the standard version supported by the organization. For security and supportability, please use:</Text><Type>plain</Type></Label><Input /></Requirement> <Requirement><Credential><Type>none</Type></Credential><Label><Text>----- If on Windows: Citrix Workspace App 2203 LTSR, latest cumulative update.</Text><Type>plain</Type></Label><Input /></Requirement> <Requirement><Credential><Type>none</Type></Credential><Label><Text>----- If on Linux: Citrix Workspace App 2211 or later.</Text><Type>plain</Type></Label><Input /></Requirement> <Requirement><Credential><Type>none</Type></Credential><Label><Text>----- If on MacOS: Citrix Workspace App 2211 or later.</Text><Type>plain</Type></Label><Input /></Requirement> <Requirement><Credential><Type>none</Type></Credential><Label><Text>You have been denied the ability to log in until the system detects a valid Citrix Workspace App client. If you require assistance, please contact the Service Desk.</Text><Type>plain</Type></Label><Input /></Requirement> <Requirement><Credential><ID>nsg-logoutBtn</ID><Type>nsg-logoutBtn</Type></Credential><Label><Type>none</Type></Label><Input><Button>Cancel</Button></Input></Requirement> <Requirement> <Credential><Type>cancelbutton</Type></Credential> <Label><Type>none</Type></Label> <Input/> </Requirement> </Requirements> </AuthenticationRequirements> </AuthenticateResponse>
-
 Michael Shuster
Michael ShusterMichael is Ferroque's founder and a noted Citrix authority, overseeing operations and service delivery while keeping a hand in the technical cookie jar. He is a passionate advocate for end-user infrastructure technology, with a rich history designing and engineering solutions Citrix, NetScaler, VMware, and Microsoft tech stacks.









