When adding administrators to your environment, you often need to limit access to specific resources in your Intune environment. Role-Based Access Control (RBAC) with scoping tags allows you to have complete control of what resources your Intune administrators have access to. Not only does limiting administrator roles with scope tags allow you to control what administrators can do, but it also allows you to control exactly which objects and policies the administrator can see and edit.
Scope Tags
Scope tags allow you to control exactly which resources your administrators have access to. They can determine the data boundaries and exactly which objects and policies an administrator can manage, and even which objects they can see. By default, resources will contain the default scope tag, and adding additional scope tags is not mandatory, but using scope tags can be a huge help to organize and control your resources.
Roles
While scope tags determine which Intune resources your administrators have access to, the role determines the administrators’ permissions in Intune. When you assign a role, it is automatically linked to the Default scope tag unless you specify others. Scope tags can be added or removed from the role assignment as needed. Most Intune administrators will already be familiar with roles, since, unlike scope tags, RBAC is used throughout the Microsoft ecosystem.
Use Cases for Scope Tags
Scope tags are great to use when you have multiple groups of administrators that require access to specific resources in Intune, but no access to other resources. Some common use cases are:
- Managed Service Providers: If you are an MSP managing multiple customers in your tenant or a customer allowing an MSP or consultant team to manage your tenant, scope tags are perfect for limiting access to the resources the outside company is accessing.
- Regional IT Administrators: If you have IT teams in different regions (e.g., U.S, Canada, Europe), you can add scopes to your Intune objects and roles, so that each team only manages and sees the objects relevant to their region.
- Testing vs Production Environments: Microsoft recommends using a dedicated test tenant for Intune. However, when that isn’t possible, scope tags can provide separation within production.
- Separating Azure Virtual Desktops: You can create a virtual device scope tag, assign it to virtual desktops and policies only, and assign it to your Azure Virtual Desktop (AVD) administrators to allow them to access the AVD resources in Intune.
Example of Using Scope Tags With a Custom Role
In this example, we will create a scope tag for virtual devices, assign it to the virtual devices and related policies in the tenant and assign the scope to a custom role for virtual machine administrators. To create a scope tag and assign it to a role, you will need to have an administrator account with the Intune Administrator role.
Creating the Groups in Intune
To assign the tag and roles for the virtual desktops and policies, we will need to create two groups. One group will contain the virtual objects, and one group will contain the administrators for those objects.
- The first group to create will be a security group for assigning the tag to Intune objects. In the Intune Admin Centre, go to Groups > New Group.
- Create a security group named Virtual.
- Set the membership to assigned. (Dynamic Device can be used to dynamically assign to devices, but this example will use an assigned group.)
- Create the next group, which will be for assigning the Administrator the role. In the Intune Admin Centre, go to Groups > New Group.
- Create a security group named Virtual Machine Admins.
- Set the membership to assigned. (A Dynamic User Group can be used to dynamically assign to administrators, but this example will use an assigned group.)
Creating a Scope Tag
1. In the Intune Admin Centre, go to Tenant Administration > Roles > Scope Tags > Create.
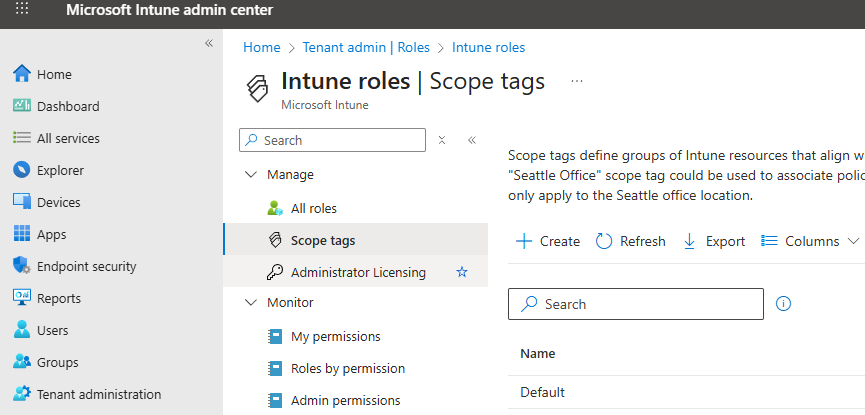
2. Fill out the basics like the name and a description.
3. Fill out the basics like the name and a description.
4. Assign the scope tag for the Virtual group created earlier.
5. Review and create.
Note: Auto scope tags assignments overwrite manually assigned scope tags. If a device is assigned multiple scope tags through group assignment, all scope tags apply.
Creating a Custom Role and Assigning The Scope Tag
1. In the Intune Admin Centre, go to Tenant Administration > Roles > All roles > Create > Intune Role
2. Name the Role Virtual Machine Administrator.
3. Select the permission you would like for the role.
4. Select the scope tags, add the Virtual scope tag, and remove the default.
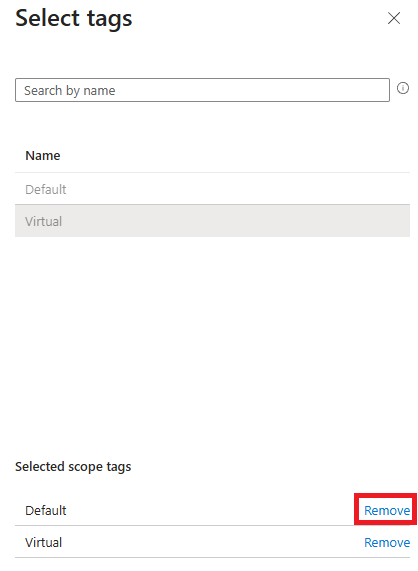
5. Review and create the scoped custom role.
6. Assign the role by going to Tenant Administration > Roles > All roles > Virtual Machine Administrator.
7. Select Assignments > Assign.
8. Name the Assignment Virtual Machine Admins.
9. Select Add Groups and the Virtual Machine Administrators group that was created earlier.
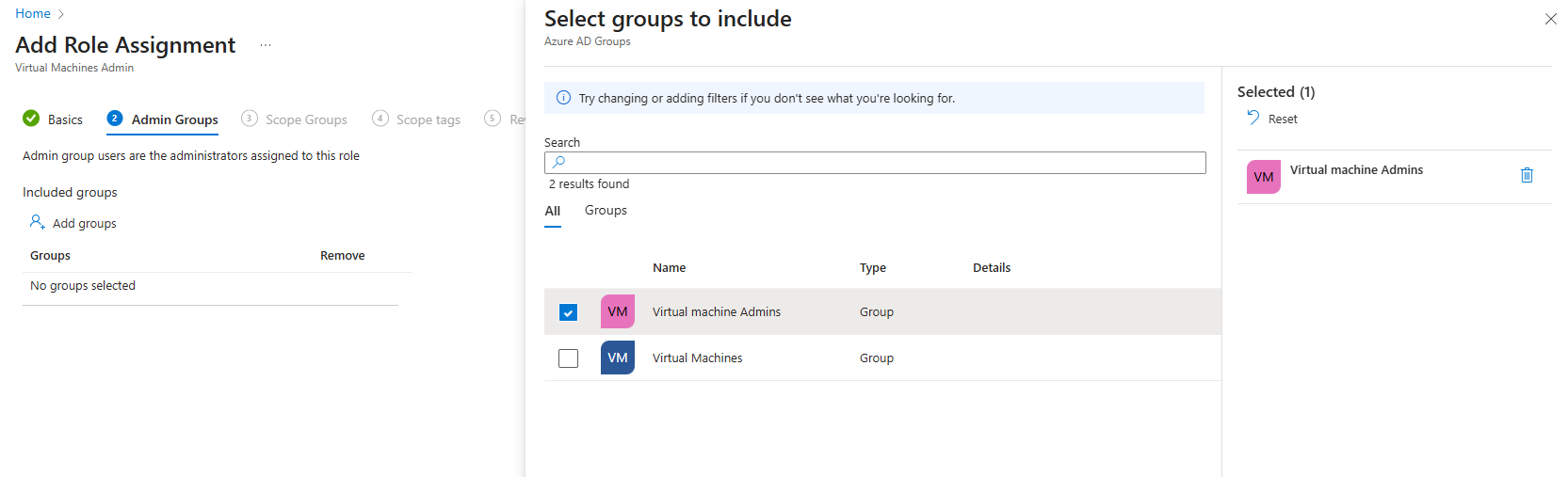
10. Select Add Groups and the Virtual Machine group that was created earlier.
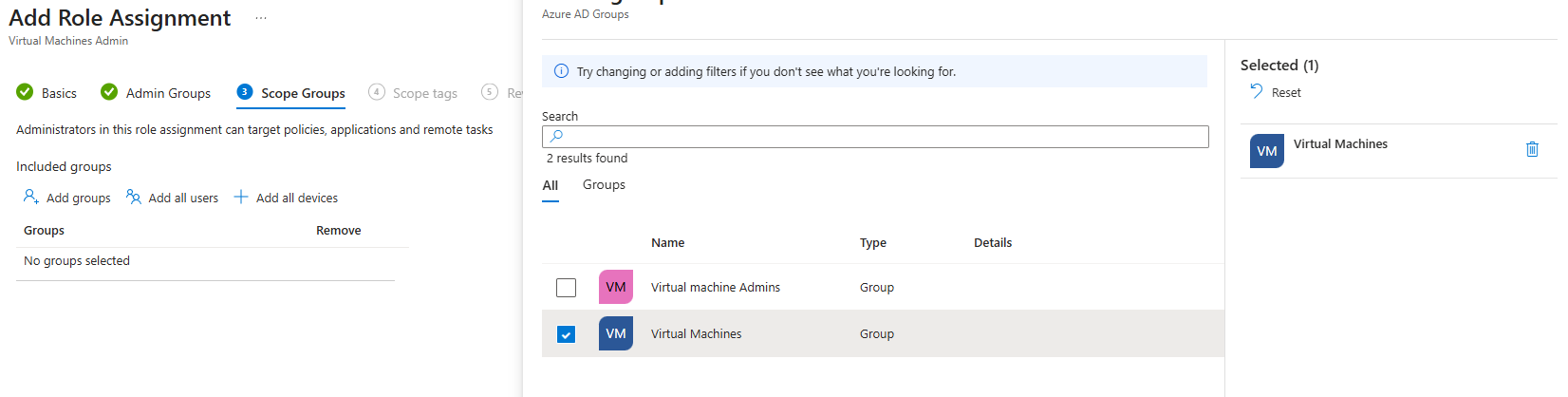
11. Select Add scope tags and the Virtual scope tag that was created earlier.
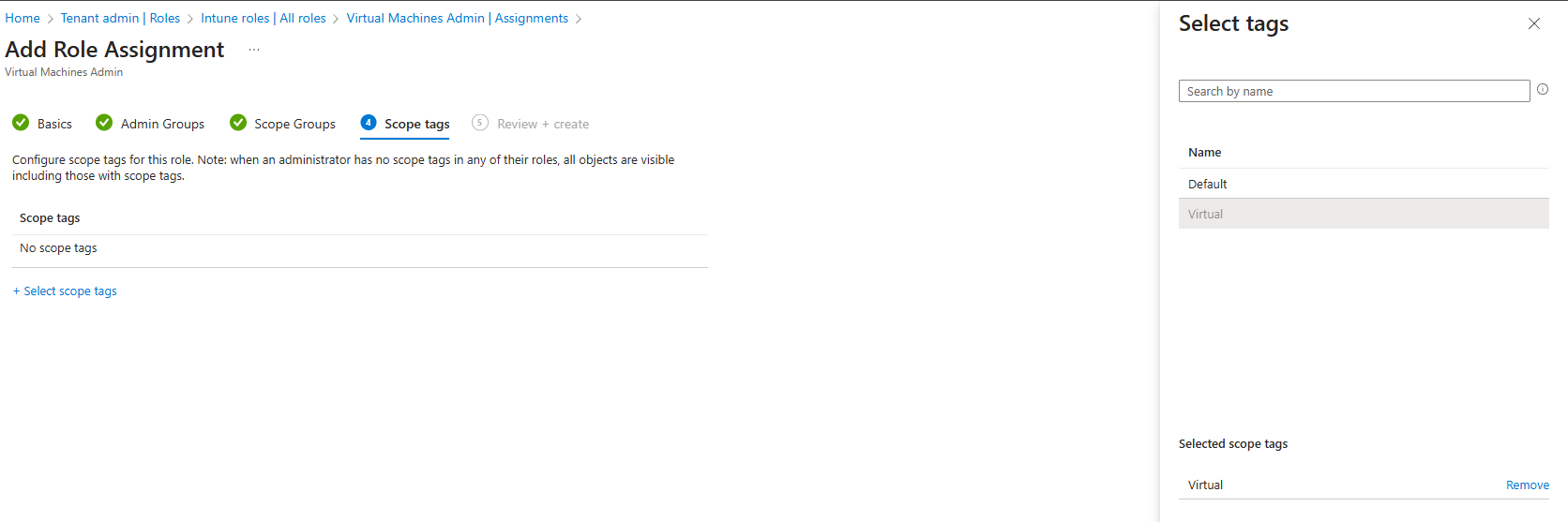
12. Review and create.
Assign The Scope Tag to Objects
Now that the scope tag is created, the role is scoped and assigned with the proper scope tag and group, we can also add objects to the scope.
1. To add a scope tag to a profile, go to Devices > Manage devices > Configuration > select a profile.
2. Choose Properties > Scope (Tags) > Edit > Select scope tags
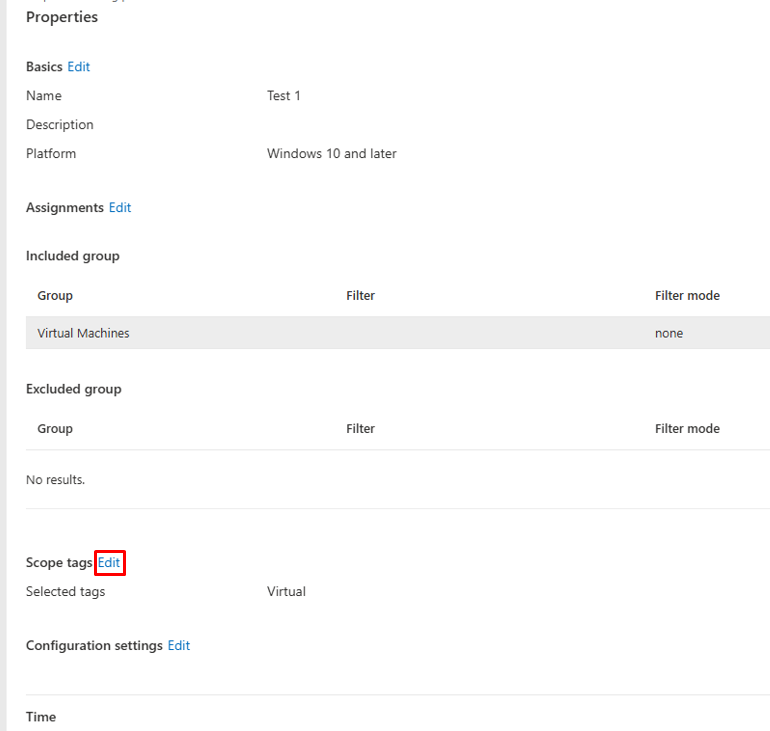 3. Edit the scope tags by searching for the name in the search for scope tags box and select Virtual.
3. Edit the scope tags by searching for the name in the search for scope tags box and select Virtual.
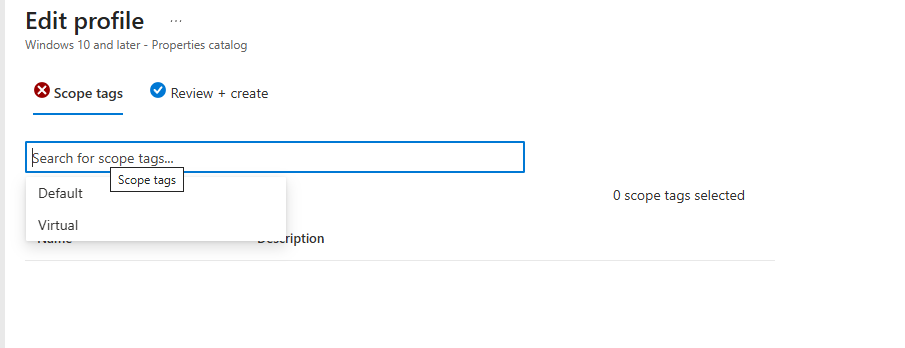
4. Review and create.
5. To add a scope tag to a device, go to Devices > Windows > select a virtual machine > Manage. properties
6. Open the scope tags.
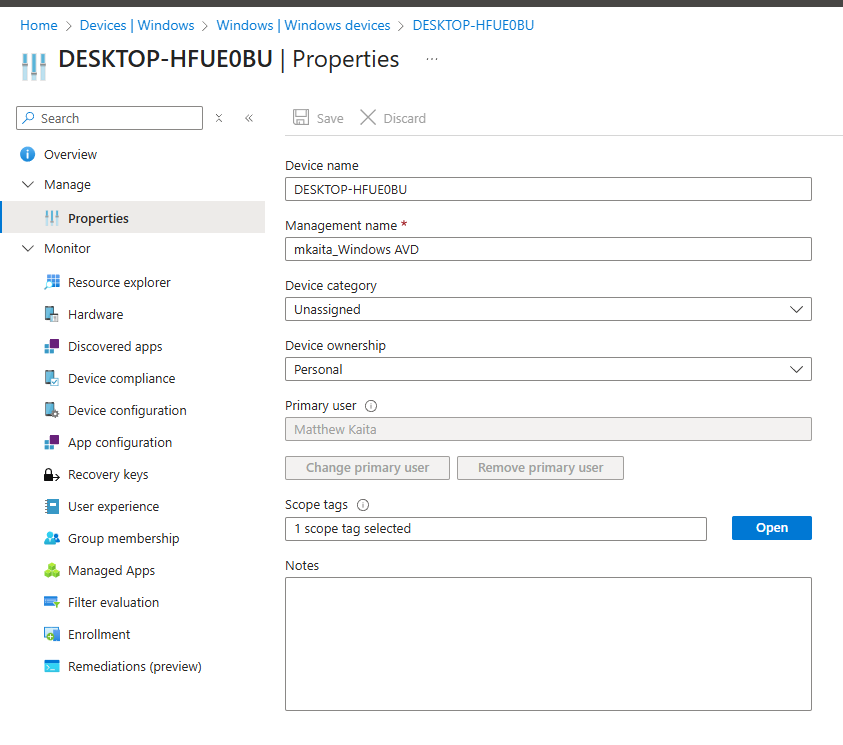
7. Select the Virtual tag and remove the Default tag.
8. Save.
In Conclusion…
Scope tags, combined with RBAC, ensure that administrative access is aligned with the organizational structure and security requirements. By defining permissions with roles and filtering access with scope tags, you create a secure, scalable Intune management model. Whether you are managing multiple clients, regional teams, or separating test environments from production, scope tags offer granular control over what administrators can see and manage. If you are looking to scale your Intune environment securely and logically, understanding and implementing scope tags should be a key part of your RBAC strategy.