The Scenario
Implementing an application firewall on a NetScaler Gateway is a leading security practice that enhances protection against web-based threats, ensuring secure and compliant access to enterprise applications. Our Canadian healthcare client uses NetScaler Gateway to provide secure remote access to their internal lab systems for a diverse group of users, including lab technicians, physicians, and administrative staff. While they already had perimeter-level App-Firewall protection, the NetScaler Gateway itself—as the initial ingress point for Citrix sessions—presented a potential vulnerability if left unprotected. It’s also important to recognize that protecting the Gateway with a third-party WAF isn’t practical unless HDX and authentication traffic are split, since HDX traffic cannot be intercepted by external WAFs. This limitation underscores why enabling App-Firewall directly on the NetScaler Gateway is both the most practical and the most operationally efficient approach.
Why Implement a New Security Model with NetScaler App-Firewall?
The existing App-Firewall, while robust, is external to the NetScaler Gateway. This separation creates several challenges:
- A policy enforcement gap at the Gateway level.
- Additional inspection hops, which introduce latency.
- Operational overhead in maintaining and synchronizing policies between separate security systems.
Integrating App-Firewall directly into the NetScaler Gateway offers a more streamlined and powerful approach:
- Applies inspection policies natively at the first point of access.
- Offers context-aware protection tailored for Citrix traffic.
- Simplifies rule management via the NetScaler management plane.
Technical Assessment
NetScaler App-Firewall is a powerhouse when it comes to web application security. It is designed to mitigate the OWASP Top 10 threats, protecting against common attacks like Cross-Site Scripting (XSS), SQL Injection (SQLi), and Cross-Site Request Forgery (CSRF). It supports both positive (allowing only known good traffic) and negative (blocking known bad traffic) security models, providing flexibility in the approach for protection. One of App-Firewall’s key strengths is its deep integration with ICA Proxy and SSL VPN traffic, which is crucial for a Citrix environment. To facilitate implementation, it has a learning mode to adapt to valid application traffic patterns and provides advanced logging and reporting via AppFlow. Dig in deeper here with the NetScaler App Firewall Deployment FAQ and Guides.
When comparing NetScaler App-Firewall to the customer’s existing solution, the benefits become even clearer:
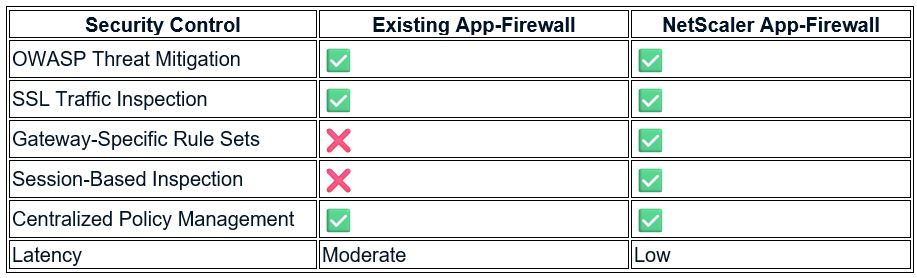
The ability to have Gateway-Specific Rule Sets and Session-Based Inspection directly on the NetScaler Gateway is a game-changer, significantly enhancing the protection at the initial ingress point.
How App Firewall Works on NetScaler Gateway for ICA Sessions and AAA vServer
This is where the magic truly happens. When App Firewall is enabled on the NetScaler Gateway, it integrates seamlessly with the ICA sessions and AAA (Authentication, Authorization, and Auditing) virtual servers. Web App Firewall protection for VPN virtual servers and authentication virtual servers.
- For ICA Session traffic: As users launch applications and desktops through the NetScaler Gateway, an ICA session is established. The App Firewall intercepts and inspects all the traffic flowing within this ICA session. This means that not only is the initial authentication secured by the AAA vServer, but also that the subsequent application traffic traversing the ICA session is subject to the App Firewall’s granular inspection policies. It can detect and block malicious payloads, protect against command injection within the ICA session, and ensure that only legitimate application interactions are allowed. This is vital for preventing attacks that might attempt to leverage an established ICA session to exploit internal systems. The App Firewall is optimized explicitly for ICA traffic encapsulation.
- For AAA vServer traffic: The AAA vServer handles user authentication. By binding App Firewall to the NetScaler Gateway vServer, which includes the AAA vServer’s authentication workflows, the App Firewall provides a crucial layer of defense even before a user is fully authenticated. It inspects login forms, protects against credential stuffing, prevents brute-force attacks, and guards against various web-based attacks targeting the authentication process itself. This means that even the very act of logging in is secured, making it much harder for attackers to compromise user accounts or bypass authentication mechanisms. The App Firewall can scrutinize elements like login forms and session cookies, XML/JSON payloads standard to Gateway interactions, and request headers and form fields used in Citrix Workspace traffic. When Web App Firewall protection is enabled, NetScaler leverages built-in profiles like ns-aaa-default-appfw-profile, which contain associated built-in API specification files to ensure traffic is secure and compliant with API specifications. You can allow WAF for all AAA vServers by setting the wafProtection parameter to AUTH.
This integrated approach provides robust protection at every stage of the user session’s journey through the NetScaler Gateway.
Operational Benefits
Beyond the technical gains, this integration of App-Firewall and NetScaler Gateway brings tangible operational advantages:
- It reduces complexity by coalescing inspection and access control.
- It speeds up troubleshooting with unified logging and analytics.
- It allows quicker response to threats targeting authentication workflows.
- It reduces overall traffic traversal within the DMZ.
Practical Guidance for Implementation
Implementing this is not as daunting as it might sound. Here is a practical roadmap:
Step 1: Bind App-Firewall to the NetScaler Gateway vServer
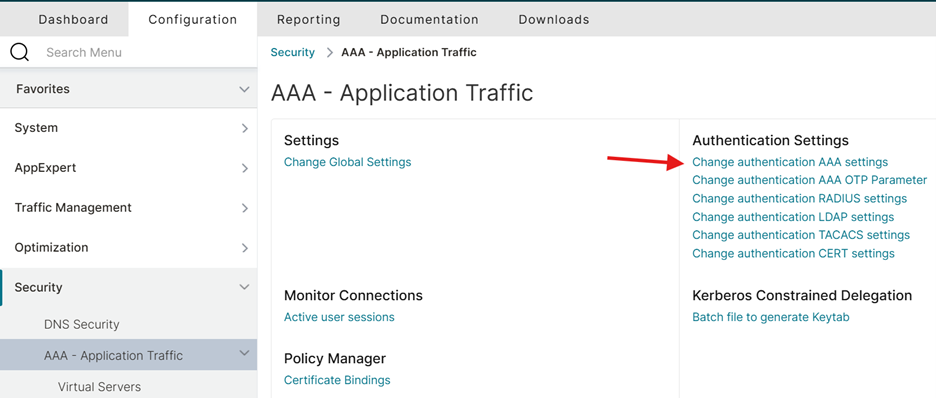
Start by binding the NetScaler App-Firewall profile to the NetScaler Gateway virtual server (vServer). For gateway protection, Citrix offers hardened and pre-tested profiles, such as the default ns_default_appfw_profile, that are already optimized for ICA Proxy, VPN, and authentication workflows. These profiles are designed to mitigate OWASP Top 10 threats while remaining fully compatible with common NetScaler Gateway use cases, including remote access authentication, SSL VPN sessions, and ICA traffic encapsulation. To configure Web App Firewall protection for virtual servers, you can navigate to Security > AAA- Application Traffic > Change Authentication AAA Settings.
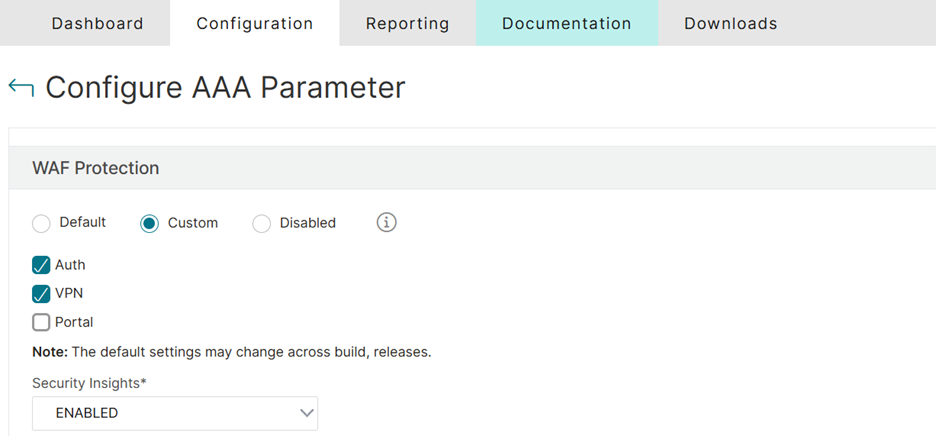
Configure WAF Protection. Options include AUTH for authentication virtual servers, VPN for Gateway virtual servers, and Portal related to web portals. In this case, we set it to AUTH and VPN to protect both.
Step 2: Use Built-In App-Firewall Templates Optimized for Gateway
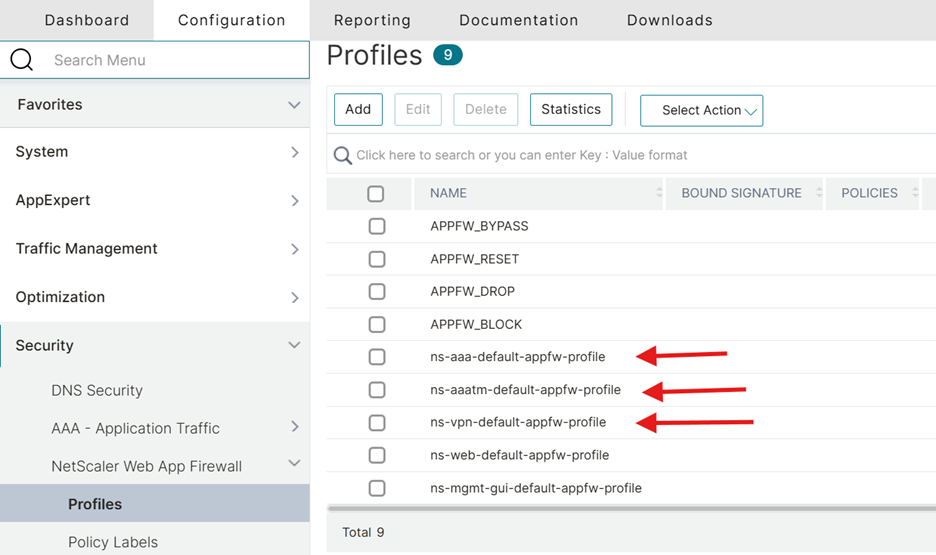
Resist the urge to jump into Learning Mode or extensive custom tuning right away. Instead, leverage Citrix’s built-in Gateway-optimized profiles. These are pre-configured to recognize and protect: login forms and session cookies, XML/JSON payloads common to Gateway interactions, and request headers and form fields used in Citrix Workspace traffic. This approach simplifies deployment immensely and dramatically reduces the risk of false positives or unexpected application breakage. NetScaler provides built-in Web App Firewall profiles such as ns-aaatm-default-appfw-profile, ns-aaa-default-appfw-profile, and ns-vpn-default-appfw-profile. These profiles contain associated built-in API specification files (e.g., ns-aaa-spec, ns-vpn-spec) to ensure network traffic is secure and compliant with API specifications. You can also import new API schema files if needed.
Step 3: Monitor with AppFlow and Citrix Analytics
Instead of relying solely upon Learning Mode for initial tuning, make good use of AppFlow and Citrix Analytics for Security (if available) to gain insights into blocked requests, threat trends (like XSS or injection attempts), and any Gateway-specific traffic anomalies. Ensure that the ULFD mode and AppFlow feature are enabled on the NetScaler. Administrators can configure an AppFlow collector by navigating to Configuration > System > AppFlow > AppFlow Collectors. Logs should also be forwarded to the SIEM (e.g., Splunk, QRadar) to ensure real-time alerting and crucial forensic visibility. The Web App Firewall supports both native and CEF (Common Event Format) logs. CEF logging can be enabled by setting CEFLogging ON for AppFirewall settings. Administrators can view Web App Firewall logs in the Syslog Viewer in the NetScaler GUI or access them from the command line interface (e.g., tail -f /var/log/ns.log). For optimal filtering in the Syslog Viewer, logs should be in CEF format. NetScaler AppFirewall: Configuration, CEF logging, Signatures.
Step 4: Validate the Integration Once the Profile is Bound and Configured.
Thorough validation is key:
- Confirm successful user login and session initiation via the Gateway.
- Confirm that legitimate ICA Proxy and VPN workflows are unaffected.
- Crucially, simulate common attack vectors (think XSS in a login URL or cookie manipulation) to confirm that blocking occurs as expected. The integrated API-based inspection engine and default profiles are specifically designed to eliminate the need for traditional App-Firewall learning cycles when applied to the Gateway.
In Conclusion
Implementing NetScaler App-Firewall directly on the NetScaler Gateway for this Canadian healthcare company is not just viable—it is strategically advantageous. It aligns with leading practices in modern secure access design, reduces architectural complexity, and improves both user experience and auditability. A truly successful implementation hinges on careful policy tuning, maintaining robust operational visibility, and seamless collaboration between the networking and security teams. The reward? A more agile, integrated, and inherently more secure infrastructure for remote healthcare access.