
Issue: Citrix Gateway Error “No IntranetIP available. Please try login later.” and Other Issues After ADC 13.0 or 13.1 upgrade
Issue and Background
After upgrading Citrix ADCs to more current Citrix ADC 12.1, 13.0, or 13.1 firmware builds from earlier releases, users may encounter a couple of issues depending on how old the configuration of the appliance is (i.e. had it gone through many major firmware release upgrades over its lifetime) or if using some legacy session policy guidance for the Citrix Gateway session policy expression. Per this Citrix discussion, it has been reported earlier this year on all supported releases after changes within each of the major firmware builds were implemented.
The first issue presents itself to users as the following message after authenticating to the Citrix Gateway, as a white background with black text:
“No IntranetIP available. Please try login later.”
Although not a fully accurate or complete list, this issue has been noted in builds based on public discussions:
- 12.1 b64.16 and later
- 13.0 b85.15 and later (possibly earlier builds)
- 13.1 17.42 and later (possibly earlier builds)
The second issue will present itself once the first issue is resolved for some customers depending on how the session policy expressions are configured. This has been encountered for a year or so now. Two variants depend on the global Citrix Gateway configuration. Either an error attempting to invoke the Citrix Java plugin, or attempting to launch the Citrix Gateway plugin even though session policies for web browsers bound to Citrix Gateway vServer (or user/groups in ADC) specify ICA Proxy ON and/or MacOS X / Windows client plugin type.
Root Cause and Resolution (Issue 1)
The root cause in both the issues appears to be a bug, or at least a change in how ADC is processing prior configs that worked fine. Bug is more likely being we’ve seen some NSHELP cases logged.
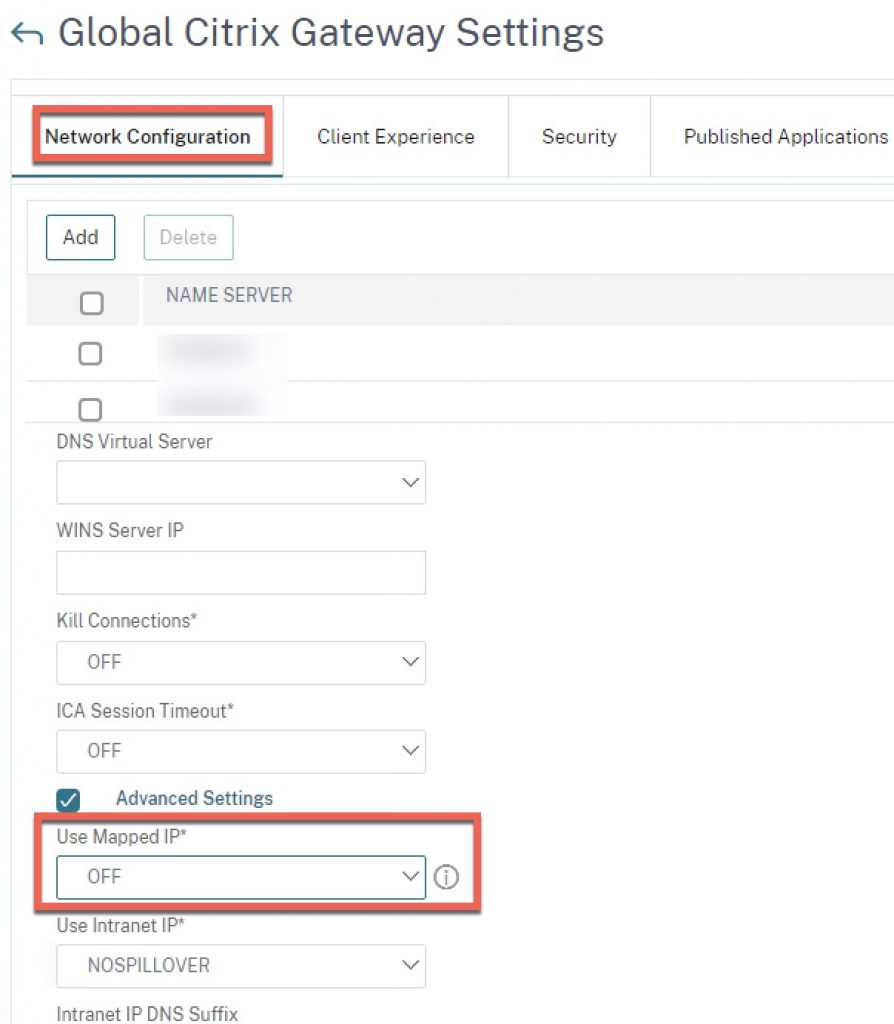
In the case of the Intranet IP issue, it appears this only affects appliances who have had the Global Citrix Gateway or session profiles network configuration set to the Mapped IP mode of “OFF” whereas more current firmware build defaults when deployed seem to set it to “NS”. Below is an example of an impacted configuration post-upgrade where the appliance configuration default was “OFF”. We suspect this may be from appliances who once had much older firmware on them and went through numerous firmware upgrade cycles (which do not always change defaults).
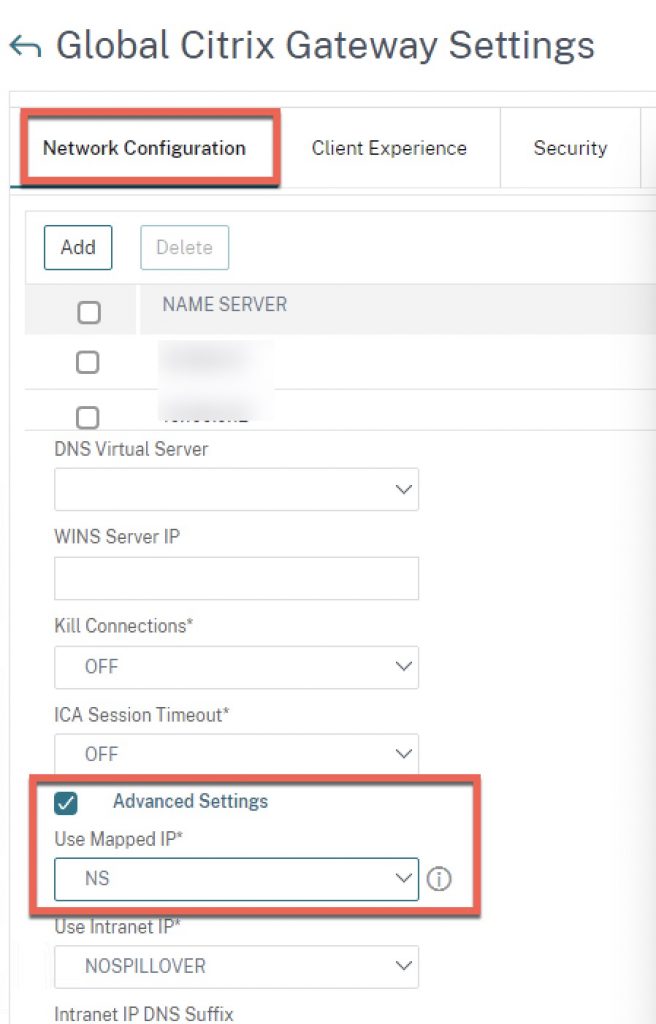
And here is the correct setting. Note that in our most recent case we swapped this globally and it worked fine, but some admins appear to have reported this caused them some issues elsewhere. If there are issues created after the change, we recommend making the change within each of your affected session policy profiles instead, setting it to “NS” instead of “OFF”. Some customers have also found a need to switch “Use Intranet IP” to “OFF” as well, however we did not need to in our instances to resume functionality.
Root Cause and Resolution (Issue 2)
In the second issue, what is happening is an expression used within the session policies (usually for web browsers) that relates to referer is not being processed by the ADC. As such the session logging in does not match the intended policy and the global defaults of the ADC apply instead. These are expressions found in numerous Citrix docs including current 13.0 and 13.1. Historically the referer expressions have not caused issues, and are not always required in customer configurations.
Examples of affected policy expressions:
Advanced:
HTTP.REQ.HEADER(“User-Agent”).CONTAINS(“CitrixReceiver”).NOT && HTTP.REQ.HEADER(“Referer”).EXISTS
Classic:
REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver && REQ.HTTP.HEADER Referer EXISTS
By editing the expressions to remove the referer checks (in bold) the policies process normally as they are matched at login.
Hopefully, these issues bring awareness to admins prior to their upgrades so they may deal with them expediently should they come up during upgrade windows.







Got hit by this one,
I come with an own workaround not seen in any place ATM.:
1- Disable hasync and haprop on both nodes & savec
2- reboot secondary node
3- failover
4- reboot the now secondary node
5- failback
We’ve not tested to remove the HTTP.REQ.HEADER(“Referer”).EXISTS though.
Citrix released a firmware 2 weeks ago that resolves this, is 13.0 88.12
Yep – took ’em long enough!
Don’t install 13.0 88.12 if you have HDX Insight
No choice until a new version comes out so might need to disable insight temporarily if it’s an issue for you. 88.12 fixes a critical CVE.
88.14 will fix this.